How could ITAM have helped the Equifax CIO?

Former CEO of Equifax Richard Smith testifies before the House Energy and Commerce Committee. Image source YouTube, click image to watch the video.
The credit rating firm Equifax suffered a security breach resulting in the loss of 140m+ personal financial records.
The CEO and CIO stepped down, the share price got hammered – and all because of an unpatched, known vulnerability.
Would ITAM data helped? Could information readily available within a modern ITAM department be able to help defend against such an attack?
We asked four ITAM experts for their views:
“If only the security team had leveraged the information that the ITAM team had cultivated”
by Fulvio Inserra, Managing Director – TMG
“As ITAM professionals, we leverage as many sources as we can get our hands on and to tell us as much about an asset as possible. These sources include the common, garden inventory and discovery solutions we all know and love (think SCCM, LANsweeper, BigFix etc), but we also leverage other data sources which allow us to understand the asset in the context of the business, including where they are (environment or physical location), who is using them (user or business service), and who is ultimately responsible for the maintenance of the asset.

Fulvio Inserra, Managing Director – TMG
In the case of Equifax, more than 143 million financial records were stolen by hackers due to unpatched Apache Strut…. A patch for this vulnerability was made available back in March, but was not applied by Equifax, leading to the breach. If only the security team had leveraged the information that the ITAM team had cultivated to proactively identify all instances of Apache Strut, then the risk could have been correctly mitigated and remediated.
In IT, we’re often guilty of working in silos, with our own tools and our own processes. But imagine if Equifax IT had collaborated and utilised the consolidated information that the ITAM team had cultivated from many sources! They would have been able to obtain a view of all installations, including the version, the physical location of the device, the business service the instance was related to and so much more.
With this information, the security team could have leveraged a register of known vulnerabilities, to assess the risk to the business and where applicable, apply the necessary patches.
Broadening the scope of traditional ITAM
Traditionally, the IT Asset Management function has been focussed on optimising the use of the organisations entitlements (hardware and software), or reducing / avoiding unnecessary spend… and we’ve done it well, but with all of this information at our fingertips, so much more can be done to ensure that organisations are not only running efficiently from a cost perspective, but also able to identify risks and opportunities that are not traditionally related to the role of IT Asset Management.
In addition to the above, the ITAM function is utterly dependent on the quality of the information presented to them by the management toolsets in the environment; therefore they spend time to ensure that all devices are inventoried.
But this logic can be extended, so that we can report on systems not running patch management software, or servers that aren’t running the correct Anti-Virus software.
In short, Equifax were extremely unlucky, but it’s a situation that has plays out time and time again. Think WannaCry, anybody? These problems are completely avoidable, if only we (IT) collaborated more.”
“Whilst IT Security are usually a separate team, there can be significant benefits by sharing ITAM data”
By Tom Watson – Managing Consultant at Group 10

Tom Watson, Senior IT Architect at Group 10 Consulting
“Many IT service management disciplines have overlapping data requirements, yet they are often treated independently. IT Asset Management (ITAM) requires the ongoing discovery of software configurations in an environment to effectively manage compliance.
Whilst IT Security are usually a separate team, there can be significant benefits by sharing ITAM data, especially when it comes to responding to security incidents. While there are some reasons to segregate ITAM data from other parts of the business, there are many examples where data and information initially collected for ITAM purposes can be of operational benefit for adjacent business streams such as Application Portfolio Management, Configuration Management and ICT Security.
In Group 10’s experience, one important example of leveraging ITAM information within the business is IT Security. Once a security vulnerability has been identified, information managed by ITAM such as software deployment, configuration, and asset data can assist by allowing an organisation to quickly report on where vulnerable software installations are located. This helps the business understand their exposure and plan the remediation. It’s important to note that this use of configuration information is only possible if the organisation’s ITAM processes are mature and up-to-date. Violations of an organisation’s security perimeter are rarely due to a single cause.
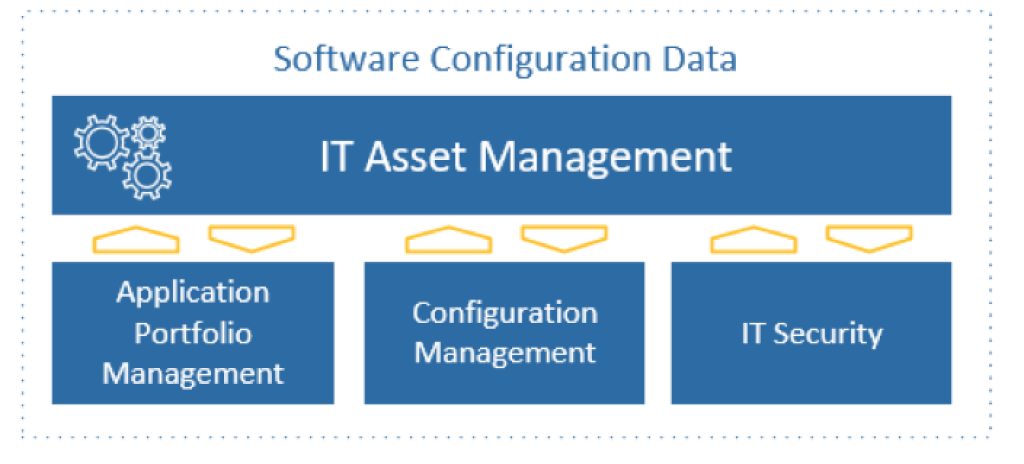
In the recent exposure experienced by Equifax, the IT teams were unable to quickly identify where the vulnerable software was installed. This was compounded by a lack of centralised patch management, and later, a discovery system that failed to identify remaining vulnerabilities. This was an example of a series of events that exposed customer data by the inability of IT teams to react in a timely manner. Upon publication of a vulnerability, ITAM teams can search the organisation’s registers of licences and contracts. This is the first crucial step to identifying if the organisation holds any entitlement to the effected product, and which business services may be at risk. In parallel, the technical teams can query the ITAM discovery tools for instances of the vulnerability. This information can then be proactively passed to security or environment management teams to commence the remediation.
The case for a central, federated, system of record
When ITAM information is held in a central or federated system, organisations are better positioned to quantify their exposure to security threats. Notable examples of ITAM tools supporting a response to a ICT Security threat include the Wannacry and Heartbleed vulnerability exploits. Once identified, ITAM teams were able to query discovery tools to find instances of vulnerable software. Normally, this sort of data would be filtered out as the vulnerabilities were not used to identify commercial titles that require licence management. Therefore, it may require specialist technical skills to identify vulnerabilities quickly. ICT Security is a complex constantly evolving discipline and one that relies heavily on accurate information.
ITAM is certainly not the panacea for managing the threat landscape but it does improve an organisation’s ability to respond. The issues and challenges faced by Equifax are another example of how important it is to have invested in implementing systems and processes that produce trusted information, so that it is on hand when dealing with an emergency.”
“Former Equifax CEO Richard Smith’s comments to U.S. Congressional leaders point to a much larger issue at Equifax –company culture”
By Philip Merson, Director of ITAM, Ivanti

Philip Merson, Director of ITAM, Ivanti
“The massive Equifax data breach could have been avoided through a layered security approach that combines Unified Endpoint Management, Security and IT Asset Management. The fact of the matter is, former Equifax CEO Richard Smith’s comments to U.S. Congressional leaders during a hearing held earlier this month in Washington, D.C. point to a much larger issue at Equifax –company culture.
It is quite clear based on his statements that Equifax does not have a culture where security is viewed as everyone’s responsibility, and the “individual failure” that Mr. Smith pointed to during his testimony is just the tip of the iceberg. This individual likely failed because having a proactive security strategy and incident response plan was not made a priority for him by his management, or by the organization as a whole. The bottom line is that based on Mr. Smith’s statements during the Congressional hearing, it does not appear as if there were any company-wide policies in place at Equifax concerning security governance. Not only that, governance and oversight clearly were not viewed as business-critical priorities by the company.
In today’s highly connected world, it’s essential the entire organization be in alignment in terms of prioritizing the importance of proactive security and putting an immediate incident response plan of action in place. In reality, many companies today face a common challenge that comes from having siloed departments within the company. For example, the web team is often separated from the security team, and the patching team is often separated from the service desk team – meaning that they are functioning using disparate tools and platforms. It is this siloed business culture that contributed to the fact that it took 40 days for Equifax to report the massive data breach, and which also points to the need for the unification of IT.
To succeed in preventing such breaches in the future, businesses must change their technology, people and processes by combining Unified Endpoint Management, Security and IT Asset Management functions for a comprehensive and layered security approach.”
“The data shows that it takes organizations 186 days, on average, to remediate a vulnerability. Meanwhile, it only takes 30 days, on average, for hackers to start exploiting vulnerabilities”
By John Emmitt, Manager, Enterprise Marketing at Flexera

John Emmitt, Manager, Enterprise Marketing at Flexera
“The Equifax data breach is a perfect example of how organizations are failing to leverage available processes and technologies to protect their data. In the case of the Equifax breach, the attack started around two months after the vulnerability was disclosed – and the patch was made available – by the Apache Foundation. That means the vulnerability could have been eliminated with a patch long before the attack. In fact, it takes much longer for organizations to mitigate vulnerabilities than it takes hackers to start exploiting them. The data shows that it takes organizations 186 days, on average, to remediate a vulnerability. Meanwhile, it only takes 30 days, on average, for hackers to start exploiting vulnerabilities. So, it’s taking organizations 156 more days to fix vulnerabilities than it takes the hackers to exploit them. We call this the ‘risk window.’ Organizations need to close the risk window to prevent breaches.
Why is identification, prioritization and remediation of software vulnerabilities such an important part of a strong security program? The reason is that exploitation of software vulnerabilities is the number one external intrusion method used in breaches, according to data from Forrester. 42% of breaches exploit a vulnerability.
How can we solve the problem and where does IT Asset Management fit into the equation? There are two parts to the risk window. First, there is the time from public disclosure of a vulnerability to when an enterprise organization becomes aware of that vulnerability. Second, there is the time from awareness to remediation of the vulnerability. To close the first gap—time to awareness, you need two things—you need to know what software is in your environment and you need to know about vulnerabilities related to that software. ITAM/SAM can provide the list of installed software assets in your IT environment, for the case where we are looking for vulnerabilities in commercial software. This list can be used by the IT Security team to let them know what software should be monitored for vulnerabilities.
Flexera’s FlexNet Manager Suite can provide the software ‘watch list’ to our Software Vulnerability Manager solution. Our Secunia Research team provides the vulnerability intelligence—also part of our Software Vulnerability Manager solution, so that organizations can quickly be aware of vulnerabilities in their environment. This closes the ‘time to awareness’ gap.
To close the ‘awareness to remediation’ gap, you need an assessment and patch management solution. Flexera’s Software Vulnerability Manager- Assessment and Patch solution enables organizations to continuously assess exposure to more than 20,000 vulnerable applications. It also lets them to prioritize, configure and publish security patches to WSUS and SCCM for hundreds of non-Microsoft applications.
Of course, in the Equifax case, the vulnerability was actually in the Apache Struts 2 open source component used in one of their applications. In this case, a software composition analysis solution can be used to scan the source code and tell you what open source and third party components are being used. These solutions can also alert organizations to vulnerabilities in OSS components. Flexera provides FlexNet Code Insight to help organizations track and manage open source software, like Apache Struts 2.”
Related articles:
- Tags: CyberSecurity · Equifax · Flexera · Fulvio Inserra · Group10 · information security · IT Asset Management · Ivanti · John Emmitt · Philip Merson · TMG · Tom Watson
About Martin Thompson
Martin is also the founder of ITAM Forum, a not-for-profit trade body for the ITAM industry created to raise the profile of the profession and bring an organisational certification to market. On a voluntary basis Martin is a contributor to ISO WG21 which develops the ITAM International Standard ISO/IEC 19770.
He is also the author of the book "Practical ITAM - The essential guide for IT Asset Managers", a book that describes how to get started and make a difference in the field of IT Asset Management. In addition, Martin developed the PITAM training course and certification.
Prior to founding the ITAM Review in 2008 Martin worked for Centennial Software (Ivanti), Silicon Graphics, CA Technologies and Computer 2000 (Tech Data).
When not working, Martin likes to Ski, Hike, Motorbike and spend time with his young family.
Connect with Martin on LinkedIn.

Interesting article, but I’m not sure how a SAM tool would be looking at a java manifest to check on Apache Struts, that would be cool, looks like Flexera have done something, but either way here are some “free” tools to help:
https://www.blackducksoftware.com/struts-threat-check?gclid=EAIaIQobChMI8qOwkLL_1gIVbhHTCh1prAoiEAAYAiAAEgLjqPD_BwE
https://nmap.org/nsedoc/scripts/http-vuln-cve2017-5638.html