Enterprise SAM Tool Certification Standard
This is an open, community-sourced standard for Enterprise SAM Tools from The ITAM Review. The purpose of this standard is to enable prospective buyers of Enterprise SAM tools to determine whether a tool meets minimum standards for Software Asset Management in enterprises. The ITAM Review certifies tools against this standard. For more on the certification process see the Appendix.
 This standard is also available as an Excel Worksheet – Enterprise SAM Tool Certification Criteria
This standard is also available as an Excel Worksheet – Enterprise SAM Tool Certification Criteria
Your contributions
We welcome community participation in this standard. If you would like to suggest additions and amendments, please email support@itassetmanagement.net. Your support and expertise are vital to improving the quality of tools and services for the whole ITAM community.Scope
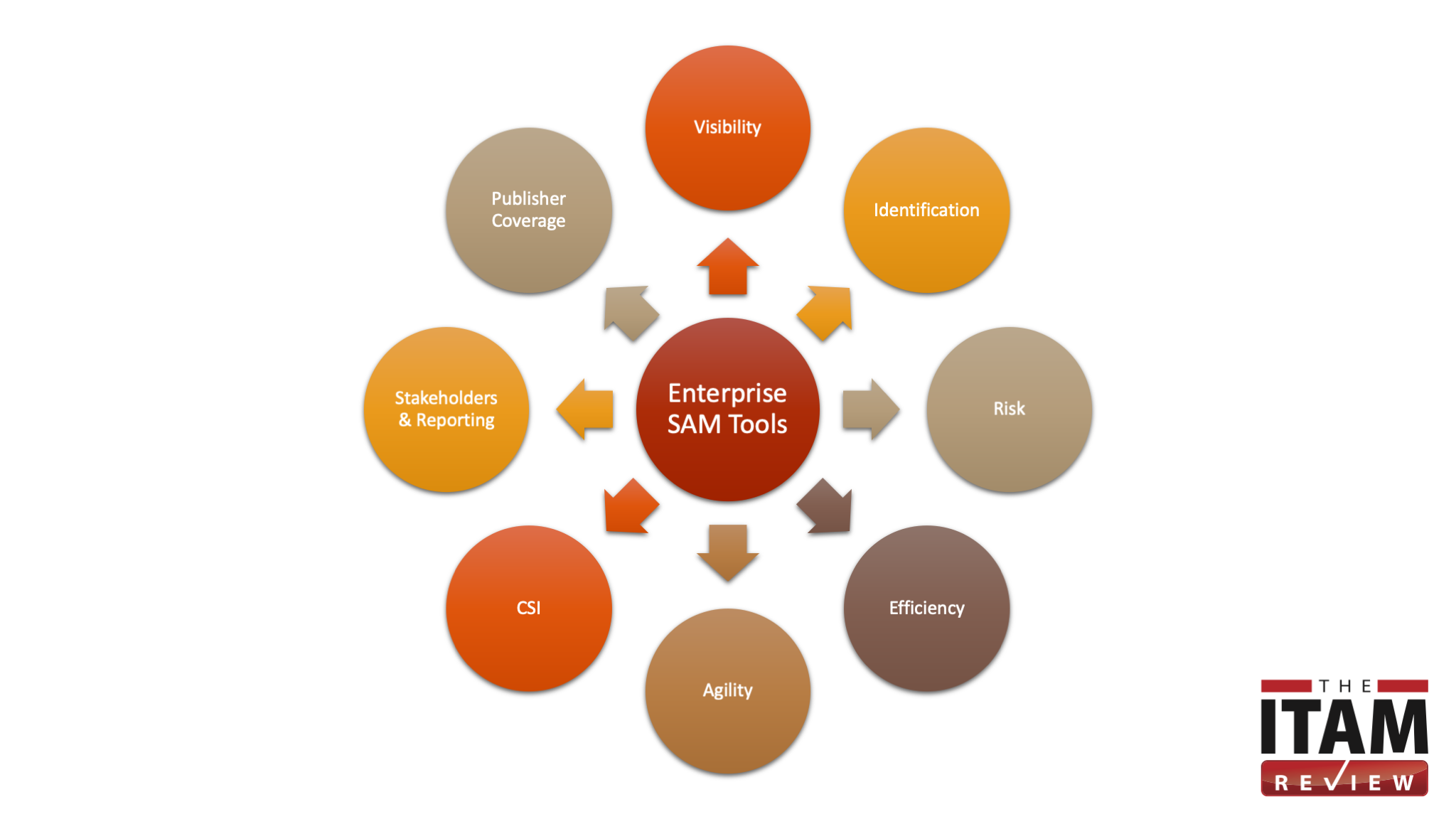
This standard covers common Enterprise SAM Tool use cases including on-premises software, datacenter, public cloud, and SaaS. It recognises the changing seniority of ITAM practitioners in organisations and the need for continuous service improvement (CSI), stakeholder engagement, and BI.Enterprise SAM Tool Certification Standard
This standard is split into 8 sections. This standard is also available as an Excel Worksheet – Enterprise SAM Tool Certification Criteria
This standard is also available as an Excel Worksheet – Enterprise SAM Tool Certification Criteria
| 1. Visibility | IT estate visibility – The ability to discover, audit, manage Inventory and demonstrate accuracy. Key competencies in this area: Audit assets, collect inventory, discover devices that have not been audited, verify the accuracy of inventory to build trustworthy inventory. |
| 1.1 | How does your product or service help clients maintain an accurate and up to date view of their IT assets and users of those assets? |
| 1.2 | How can a customer tell if they are getting adequate coverage and regular auditing of their estate? What operating coverage is available? What types of devices? |
| 1.3 | If an inventory solution is provided – How does the inventory tool communicate with assets? (Agents, Agentless, etc.) |
| 1.4 | If an inventory tool is NOT provided – how does your product or service deliver inventory accuracy using existing customer inventory sources? |
| 1.5 | How does your product or solution identify duplicate records, retired machines or machines that have gone missing? |
| 1.6 | How can customers identify when new devices are added to their environment or new users are detected? |
| 1.7 | What is the process for discovering new machines / platforms / users to the customers network? How does your product or solution help to classify and manage them? |
| 1.8 | How does your product or service track and manage the existence and usage of virtual platforms & operating systems? How does your product or service help customer manage the relationships between virtual machines or services, physical devices, users and locations? |
| 1.9 | How does your product or service provide visibility of public cloud deployments (e.g. AWS, Azure, GCP)? Which public cloud providers can you discover? |
| 1.10 | How does your product or service provide visibility of SaaS applications? |
| 2. Identification | Identifying customer IT assets – recognising software, interpreting product use rights, managing license types, procurement records. Key competencies in this area: Recognise software titles from raw technical data. Identify the product use rights for each software title, manage entitlement statements from software publishers and integrate with procurement systems. Manage complex license types and bespoke negotiated clauses. |
| 2.1 | Describe how your product or service recognizes the software installed and in use within a customer environment? Does this require use of additional technology or leverage existing sources? |
| 2.2 | How does your technology or service allow customers to prioritize risk and sort software? |
| 2.3 | Does your product or service supplement discovered software with any additional intelligence? (SKU, Price, Category, Risk etc.) |
| 2.4 | How does a customer reconcile their entitlement data with discovered software? |
| 2.5 | What approach is suggested for making use of multiple procurement systems to aid the reconciliation process? |
| 2.6 | How are different license types & usage rights managed within the reconciliation process? |
| 2.7 | How does your product or service maximimise the product use rights of a customers’ investment in software? |
| 2.8 | What approach is suggested for storing license records, contracts and additional information associated procurement records with your product or service? |
| 2.9 | How does your product or service handle the nature of a customers’s global agreements? (Global agreements, local agreements, multiple territory, multiple language, parent / child / other dependencies etc.) |
| 2.10 | Does your product or service directly integrate with publisher sources of entitlement data? If so, which publishers are supported? |
| 3. Risk | Software portfolio risk – reconciliation, risk and compliance, prioritization, accuracy. Key competencies in this area: Management reporting on compliance risk. Prioritising risks. Suggesting remedial action or most pressing issues to address. |
| 3.1 | What intelligence is provided to a customer to assess their compliance position, negotiate contracts and remove risk? |
| 3.2 | How does your product or service cater for different levels of authority and access to a customers global software risk profile? |
| 3.3 | How does your technology cater for multiple stakeholders in terms of risk management? For example, does it enable department level risk profiles to be shared with department heads? |
| 3.4 | How does your product or service support the optimal use of software across cost centres and business units? How does your product or service account for internal accounting of software versus external auditor accounting of risk? |
| 3.5 | How are customers alerted to specific risk thresholds or made aware of progress with your product or service? |
| 3.6 | What information or support is provided to improve their risk position on an on-going basis (Rather than just presenting the current risk position) |
| 3.7 | How does your product or service support identification of risks other than license compliance risk? For example, patch levels, support status, vulnerability reporting |
| 4. Efficiency | Ensuring efficient spend – redundancy, overlap, cheaper alternatives, spend analysis, contracts preparation. Key competencies in this area: Reporting on what applications are not being used, initiating work flows to remove software based on usage, identifying suite or functional overlap, suggesting cheaper alternatives, helping make smarter decisions on maintenance or subscription renewals, benchmarking spend against peers. |
| 4.1 | How does your product or service deal with usage (users making use of software versus those which are unused) How is usage calculated? How is the usage of software linked to users and / or devices? |
| 4.2 | What does your solution offer to support the removal of unused software? |
| 4.3 | How does your technology support maintenance renewals, contract negotiations and ensuring customers are deriving best value from subscriptions? |
| 4.4 | What information does your offering provide to assess if customers have architected their environment in the optimal way to ensure the most efficient spend whilst meeting technology / business service goals? i.e. could a customer re-architect certain systems to reduce spend whilst meeting business objectives and staying compliant with license terms? |
| 4.5 | What information does your product or service provide to benchmark software spend and negotiated terms against industry peers? |
| 4.6 | What intelligence does your product or service provide to help customers consolidate, reduce or optimise agreements? |
| 4.7 | What intelligence does your offering provide to highlight inappropriate product suite usage e.g. using a more expensive edition or version when a cheaper version or editon would suffice. |
| 4.8 | What intelligence does your product or service provide to help consolidate a customer software portfolio and remove redundant or duplicate applications? |
| 4.9 | What functionality is provided to enable clients to identify options for optimising spending on public or hybrid cloud? For example, Cloud BYOL |
| 4.10 | What functionality is provided to enable clients to identify options for optimising spending SaaS applications? E.G. downgrading to lower/cheaper editions based on feature usage |
| 5. Agility | Helping customers become more agile in delivery and management of software via service request automation, financial transparency, ITSM integration, scenario modelling and levers for change. Key competencies in this area: Service request automation, approved software catalogues, automated approval and removal processes, change management integration and awareness, ITSM lifecycle integrations, Asset register, management of full lifecycle, scenario modelling, advanced reporting, internal markets, charge back / show back features. |
| 5.1 | How does your product or service support architectural decision making process and deployment of new projects? (Scenario modelling, whatif analysis) |
| 5.2 | Does your product or service provide a service catalogue, automated approvals process or online shopping cart/app store facility? |
| 5.3 | Does your offering integrate with or complement existing service desk systems? Does it integrate with other systems such as Contract Management or Finance? |
| 5.4 | How does your product or solution integrate with customer joiner, mover and leaver (JML) processes? How does it track the live status of users and customers of IT? Does it enable automated deployment and harvesting of software based on JML inputs? |
| 5.5 | How does your product or service track the lifecycle of assets through the whole lifecycle (hardware and software) from request to retirement, destruction or removal? |
| 5.6 | Does your product or service enable automated optimisation of public cloud and/or SaaS deployments? |
| 6. CSI | Continual SAM Service Improvement. Process Performance, Root cause analysis, business plan performance. Key competencies in this area include monitoring process performance and governance, root cause analysis, business plan performance, KPI dashboards and management reporting. |
| 6.1 | How are exception reports generated against agreed thresholds? |
| 6.2 | How does your solution help customers monitor their progress against their SAM plan? |
| 6.3 | What intelligence is provided to customers for identifying root causes which might be causing underlying compliance issues? |
| 6.4 | What intelligence does your product or service provide to highlight a customer’s current SAM maturity and make progress? |
| 6.5 | How can a customer tell if their SAM processes are working and whether leaks are occurring? |
| 7. Stakeholders & Reporting | ITAM teams now have an increasing number of stakeholders to manage. This increases the need for accurate reporting & dashboarding. Increasingly, as C-Suite take a greater interest in the outputs from an ITAM team dashboarding & Business Intelligence becomes important. |
| 7.1 | How does your product or service account for the need for department or stakeholder-level SAM reporting? |
| 7.2 | How does your product enable stakeholders to self-service, noting the need for confidentiality between stakeholders and authority levels? e.g. providing departmental dashboards |
| 7.3 | How does your product make SAM data available to external reporting tools such as PowerBI or Tableau? |
| 7.4 | Does your product have a reporting API available? |
| 7.5 | Are users able to generate their own custom reports? Are these reports saved for ongoing use? |
| 7.6 | Are reports and dashboards available that provide insights based on baselines and trend information? |
| 8. Publishers | Please detail your experience and competency relevant to these Software publishers. |
| 8.1 | Adobe |
| 8.2 | Attachmate / Microfocus |
| 8.3 | Autodesk |
| 8.4 | IBM |
| 8.5 | Microsoft |
| 8.6 | Oracle |
| 8.7 | Quest |
| 8.8 | Salesforce.com |
| 8.9 | SAP |
| 8.10 | ServiceNow |
| 8.11 | Symantec |
| 8.12 | Veritas |
| 8.13 | VMware |
| 8.14 | Zoom |
Appendix
Certification Process
Tool providers may engage with The ITAM Review to submit their tool for certification. The certification process is as follows:- Complete a survey based on the questions in this standard
- Provide a detailed product demonstration to an ITAM Review analyst proving that the tool or service meets the certification standard
- Supply two customer references willing to discuss their use of the tool with an ITAM Review analyst
Certified Enterprise SAM Tools & Services

USU Software Asset Management Certification – Enterprise SAM
January 31, 2021
No Comments
Read More »
