Internet of Things devices: The number one attack target on the internet
F5 Networks, the long-standing networking and application services vendor, recently released the latest in a series of reports tracking the Internet of Things (IoT) security landscape; it makes for a fascinating, and worrying, read. It’s clear the pervasiveness of these internet connected devices means they are becoming integral in many critical parts of our infrastructure, and it is only going to continue to grow.
Current Scenario
According the F5 Networks report, IoT devices are now the #1 attack target on the internet, and telecom companies and hosting providers are the organisations most under attack. Geographically, Spain was the country that suffered the most attacks – with 80% of attacks in the monitored period (it has been #1 for the last 18 months) while Brazil was the top attacking country – followed by China, Japan, Poland, and the USA. Interestingly, the attacks hitting Spain were also seen hitting other countries around the world, indicating that rather than Spain being a specific target, there is simply an IoT security issue among Spanish devices and networks.
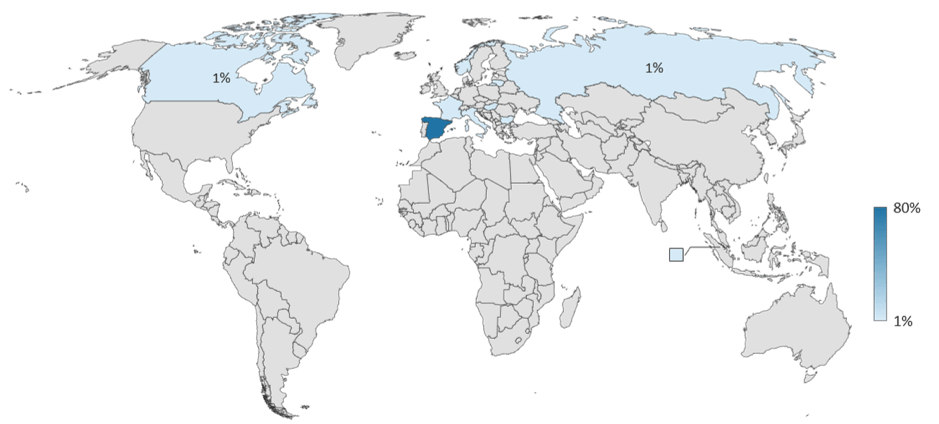
1. Top 10 attacked countries – via F5.com – https://www.f5.com/labs/articles/threat-intelligence/the-hunt-for-iot–multi-purpose-attack-thingbots-threaten-intern
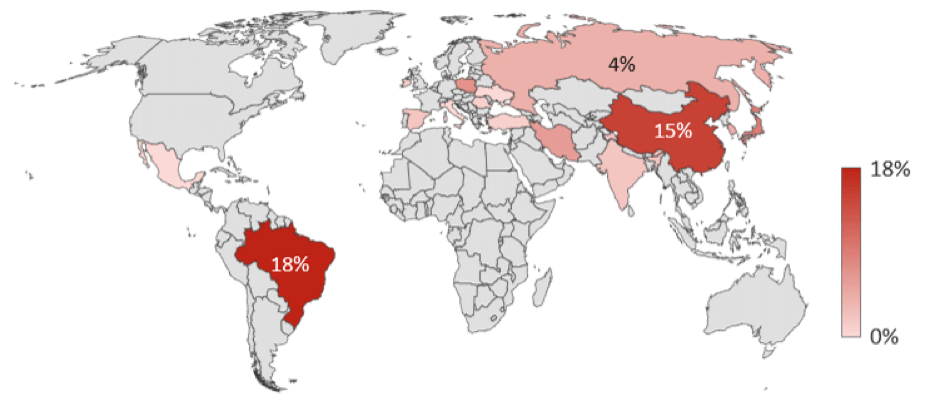
2. Top 10 attacking countries – via F5.com – https://www.f5.com/labs/articles/threat-intelligence/the-hunt-for-iot–multi-purpose-attack-thingbots-threaten-intern
What can happen?
Internet of Things devices hugely increase your organisation’s “attack footprint” – meaning more areas are exposed to the outside world, and potentially attack. No longer can one concentrate solely on “computers” as, with IoT, almost everything is a computer. For example, the digital displays used to display flight information at Bristol Airport were compromised and ransomware was installed. Bristol Airport chose not to pay the ransom but had to use manual methods for 2 days while normality was restored. Could a larger airport have taken the same course of action? Probably not.

3 Bristol Airport using pen and paper during ransomware attack. Image Credit: Julieanne McMahon via BBC News – https://www.bbc.co.uk/news/uk-england-bristol-45539841
Thingbots
Many compromised devices are used to create “Thingbots”, an IoT version of a Botnet –100s or 1000s of devices being used together to launch Distributed Denial of Service (DDoS) attacks, spread malware such as Mirai and, as we’ve already seen in Bristol, install ransomware. Other uses for compromised IoT devices include:
- Spy within organisations – as well as regular CCTV, think of all the devices which have cameras and/or microphones in them.
- To steal data across the network – being able to see passwords, corporate data, trade secrets, intellectual property etc.
- Cause business disruption – a delivery business with no way to communicate with drivers, for example
- Public service disruption – trains and trams unable to run as signal boxes have been rebooted
Another possibility is these devices being targeted for terrorist/warfare purposes, particularly within fields such as energy, water, pharmaceuticals etc. A great real-world example is that of the Stuxnet virus, believed to have been created to target Iran’s nuclear weapon program. Researchers believe the malware was used to change the speed of uranium-enriching centrifuges until they were destroyed. Almost 1,000 centrifuges were removed from the program, significantly slowing progress towards their goal.
ITAM
For IT asset managers in certain industries, this kind of threat must seriously be considered when deploying and managing assets, particularly Internet of Things devices. The more ways into your environment, the more problems you’re likely to experience – especially when those ways in are poorly built and difficult to manage. A common attack vector is IoT devices using the default, built-in admin credentials, many of which are extremely basic. F5 show the top 5 attacked credentials are:
- root:root
- admin:admin
- user:user
- test:test
- ubuntu:ubuntu
which, as F5 put it, “should never be default credentials to begin with” – 88% of the top 50 attacked credentials had the same username and password!
F5 have also seen attack traffic coming from a Keurig coffee maker, which shows how wide the definition of “IT Asset” is becoming as we move into 2019 and beyond.
Isn’t this security?
Yes – but isn’t security intrinsically linked with ITAM?
A key part of managing an asset is ensuring it is secure…if a building manager left the doors hanging off their hinges, there would be problems. Even if there was a separate “door upkeep” team, the expectation would surely be for the two to work closely together – just as ITAM and security teams should.
At some point, it will probably become critical that your organisation can locate every single IoT device it has – perhaps to issue an emergency patch, or change the login details, or to shut them down pro-actively – or something else. Whatever the reason, ITAM is best placed to have the tools and know-how to generate that data. Get involved now – make sure the business understands the risks of IoT, and work with your security teams to put a plan in place before it’s too late.
Further Reading
F5 Threat Intelligence Report – https://www.f5.com/labs/articles/threat-intelligence/the-hunt-for-iot–multi-purpose-attack-thingbots-threaten-intern
Bristol Airport – https://www.infosecurity-magazine.com/news/bristol-airport-hit-by-ransomware/
Bristol Airport on BBC – https://www.bbc.co.uk/news/uk-england-bristol-45539841
Stuxnet and Iran – http://isis-online.org/uploads/isis-reports/documents/stuxnet_FEP_22Dec2010.pdf
Related articles:
Hardware Remains Top IT Spending Category
How could ITAM help Travelex restore service?
ITAM tool & service acquisitions continue - SolarWinds, SoftwareOne, & Moveworks
Improve Your IT Asset Management Controls or Face Unbudgeted Costs
Bridging the Gap – how to build a process for Datacenter Change Management, PMO, & ITAM
ITAM during a crisis: back to basics
- Tags: F5 Networks · Internet of Things · IoT · security · Security attacks
About Rich Gibbons
A Northerner renowned for his shirts, Rich is a big Hip-Hop head, and loves travel, football in general (specifically MUFC), baseball, Marvel, and reading as many books as possible. Finding ways to combine all of these with ITAM & software licensing is always fun!
Connect with Rich on Twitter or LinkedIn.
