Gambling on Microsoft Custom Support for Windows Server 2003
This article was contributed by Paul DeGroot, Principal Consultant at Pica Communications.

Paul DeGroot
Paul DeGroot is one of the world’s leading experts on Microsoft licensing principles, policies, and strategies. He led the licensing practice at Directions on Microsoft, and subsequently formed Pica Communications, LLC to deliver exceptional insight into Microsoft licensing for audiences and organizations worldwide.
In his role as Senior Consultant at Software Licensing Advisors, he has led customers to more than $250 million in negotiated savings over the last three years.
Paul will be in London, delivering an intensive 3 day Microsoft Licensing & Negations Workshop, a fantastic opportunity for anyone looking to improve their Microsoft knowledge from 19th – 21st October. For more information and how to book, click here.
Interested in Microsoft Licensing? Attend one of our FREE upcoming one day Seminars in London or New York!
Gambling on Microsoft Custom Support for Windows Server 2003
As the clock ticks down to July 14, 2015, many Microsoft customers are wondering how much to gamble on 12-year-old servers. Microsoft wants as much as as $3,000 per server to maintain support on Windows Server 2003 for the next year, and those costs will rise 50% to 100% per year.
The good news: if you analyze the risks, the case for gambling is quite good.
Microsoft’s Support Life Cycle
First, why is this happening?
Microsoft’s life cycle policy consists of two major support phases plus two options for support after those end.
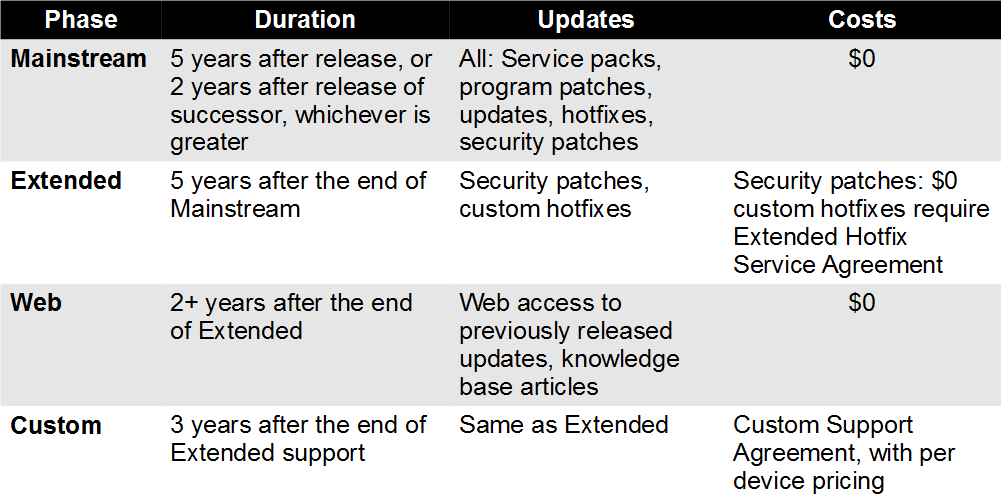
Caption: As products age and upgrades appear, Microsoft charges customers more for assured support. Security hotfixes and updates are available for the full 10-12 years of Mainstream and Extended support, but after Extended support ends, customers must decide whether to pay for critical hotfixes.
Windows Server 2003’s end-of-life date was extended two extra years because its successor, Windows Server 2008, was not released for five years, but many customers still feel squeezed between extortionate support costs and application inflexibility. Some Windows Server 2003 instances are part of complex solutions that include costly hardware, such as point-of-sale systems in retail environments, diagnostic equipment in hospitals, or robotic controls in assembly or processing plants. Upgrading the server OS may cause the system to fail or void the warranty. Not upgrading may run afoul of regulations, such as the U.S. Health Insurance Portability and Accountability Act (HIPAA) or the Payment Card Industry (PCI) Data Security Standard for handling credit card transactions, which require strong network and data security.
Microsoft Custom Support Agreements (CSAs) provide ongoing support for customers who are unable to retire old products on time. Each agreement covers a specific Microsoft product, such as SQL Server 2000, Windows XP, or Windows Server 2003.
To provide further encouragement to upgrade, CSAs are extraordinarily expensive. Many customers will pay more for one year of CSA on Windows Server 2003 than they paid for the original server license plus 12 years of Software Assurance.
A Custom Support Agreement includes the following:
- “Critical” and “Important” hotfixes or updates
- Ongoing problem resolution for solutions that include Windows Server 2003
- Custom hotfixes for critical problems
Critical non-security hotfixes are defined as problems that cause significant business loss or degradation of service, including crashes, loss of data, or functional instability. Critical security vulnerabilities can result in remote code execution, elevation of user privileges, or denial of service, without user prompts or action. Important security vulnerabilities can cause similar problems but may require user action and may offer prompts that the user must click on.
Customers must sign up for support for a minimum of 100 servers and must also have a separate Premier Support Agreement.
CSAs, unlike most Microsoft agreements, can be purchased retroactively. For example, a customer could wait until Dec. 31. 2016 to purchase a CSA, but they would be charged retroactively to July 15, 2015, and would receive any critical or important hotfixes that Microsoft released since then.
An alternative to the CSA is Custom Support Essentials—rarely mentioned because it will cost customers, and benefit Microsoft account teams, less. It has an enrollment fee that costs about 15% of a CSA (in our experience), and a fee for each device that uses an hotfix. One hotfix is included in the fee, and additional hotfixes can purchased for a modest fee although the per-device application of a hotfix is still costly.
Unlike the CSA, the CSE does not include “important” hotfixes and is not retroactive, so customers who wait until a critical hotfix is released will need to purchase a CSA to get it.
In one analysis we did, a one-year CSE on 100 SQL 2000 servers cost $1.3 million while a comparable one-year CSA cost $3.1 million.
Calculating the Risk
Customers who don’t purchase a CSA will not have access to critical hotfixes immediately, but what will they lose? Windows Server is a mature product, Only one critical non-security update has been released in the last 30 months, and the number of critical security updates is on a downward trend.
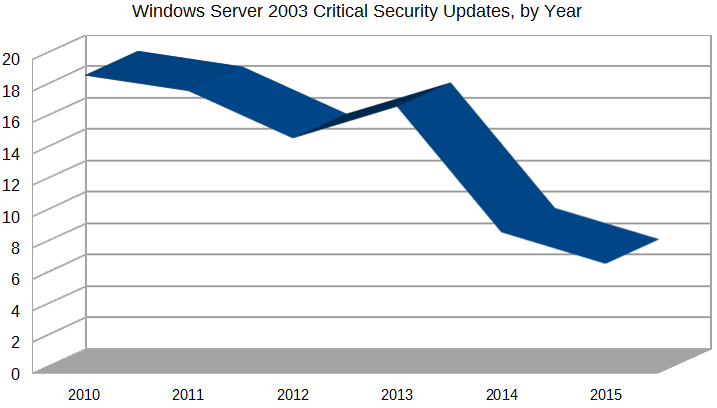
As Windows Server 2003 matures, critical hotfixes become less frequent and can be expected to decline in the future. Note that 2015 data covers only the first half of the year.
Furthermore, not all critical updates are equal.
- Windows Server 2003 shares most of its code with Windows XP (common with Microsoft desktop and server OSs released close together) and many critical updates for Windows Server apply mostly to common desktop usage scenarios. For example, the only critical non-security update for Windows Server in the last 30 months fixes ASP.net pages that don’t display properly. If the server doesn’t deliver ASP.NET pages, this update provides no value.
- Ensuring that server administrators don’t use a Windows Server 2003 console to look at pictures, listen to music, read email, or browse the Web can eliminate most Windows Server 2003 critical risks. Of 85 critical security updates in the last five years, 72 require someone at the server console to do something, such as click on a link, open a media file, or access a Web page that uses a particular font. If administrators need such access, they should use a client PC or a separate account with no domain or administrative privileges, which reduces the scope of damage if an attacker gains control of the console.
- Twenty percent of critical security updates fix problems associated with Microsoft development platforms, such as the .NET Framework, Silverlight applications, and XAML (Extensible Application Markup Language) pages. A Windows Server 2003 server that does not use these platforms is less vulnerable to exploits that attack them.
(For details of all critical security updates for Windows Server 2003 released since the start of 2010, see the list put together for Software Licensing Advisors here).
A CSA Strategy
Our recommended strategy for handling Windows Server 2003 issues involves the following steps:
- For any Windows Server 2003 servers that will continue to run after July 14, 2015, review the list of critical updates and give the highest priority to mitigating common vulnerabilities. Turn off unneeded secondary services (like SMB, Telnet, and print spooling), migrate .NET applications to new servers, and eliminate console use for all except essential administrative tasks.
- Do not purchase a CSA—yet. Customers may never get a critical update that applies to their servers. In the meantime they should decommission Windows Server 2003 servers as quickly as possible. If an applicable critical update is released in the future, the number of still-running Windows Server 2003 instances will be much smaller and a retroactive CSA will cost less.
- Consider a CSE rather than a CSA if immediate support is still required or recommended.
Customers who advise Microsoft that they will not purchase a CSA immediately put themselves in a much stronger bargaining position, as happened with CSA hold-outs on Windows XP. Discounts of greater than 90% magically appeared as the deadline approached.
Customers should also look at fundamental architectural changes that may help them avoid the CSA crunch in the future.
- Stop building custom applications that depend on proprietary server and user device OSs. Apps written in HTML, Java or other browser-accessible technologies reduce OS dependence. They sidestep a thicket of costly Microsoft licensing restrictions and can be accessed by virtually all mobile and desktop devices.
- Encourage vendors to support Web interfaces and alternative databases and servers. Vendors who insist that their product runs only on Microsoft, IBM, or Oracle databases and can be managed only from a Windows 7 desktop are planting a financial time bomb in your IT budget.

Paul DeGroot
Paul DeGroot is one of the world’s leading experts on Microsoft licensing principles, policies, and strategies. He led the licensing practice at Directions on Microsoft, and subsequently formed Pica Communications, LLC to deliver exceptional insight into Microsoft licensing for audiences and organizations worldwide.
In his role as Senior Consultant at Software Licensing Advisors, he has led customers to more than $250 million in negotiated savings over the last three years.
Paul will be in London, delivering an intensive 3 day Microsoft Licensing & Negations Workshop, a fantastic opportunity for anyone looking to improve their Microsoft knowledge from 19th – 21st October. For more information and how to book, click here.
Interested in Microsoft Licensing? Attend one of our FREE upcoming one day Seminars in London or New York!

As a MPN solution provider, this CSA is problematic. For OS level tools like ours, some patches require an update. Have not been able to find anyone associated with MPN that knows of a partner program for these patches and hotfixes related to OS that are officially out of support.
Any one have any ideas here?