Hard drive disposal best practice – Community survey results
Thanks to everyone that took the time to respond to our quick poll on hard drive disposal (Original request here).
The goal was to understand how ITAM Review readers dispose of hard drives, the methods used, standards adhered to and attitudes towards hard disk disposal.
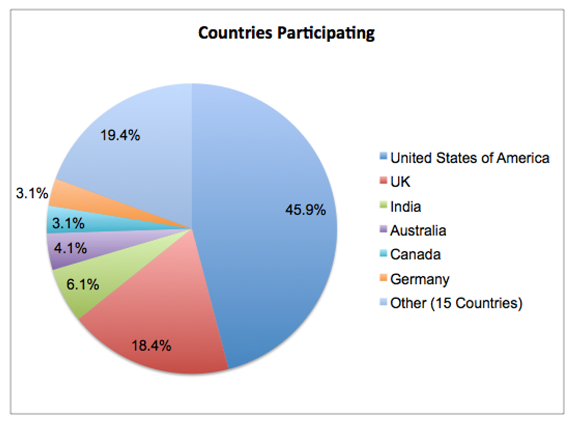
I closed the poll after we reached 100 respondents. Results were from 21 countries with the lion’s share coming from USA and UK as per below:
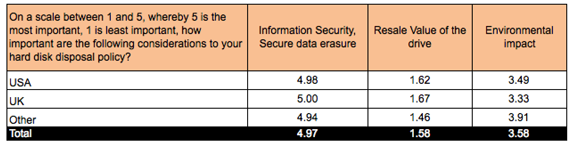
Key Considerations when disposing of hard drives
Information Security and the secure erasure of data was overwhelmingly the strongest consideration with 99% of respondents citing it as a very important consideration. Environmental impact was secondary with an average score of 3.58 (1 is least important, 5 is most important) and the resale value of drives were of little consideration with a global average of just 1.58.
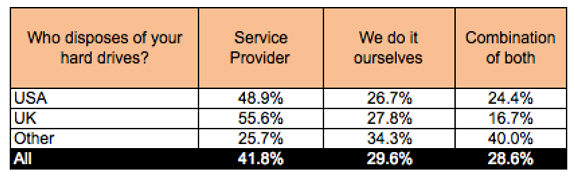
Asset disposal partners
Roughly half of organizations polled are using a service provider to assist with disposal of hard drives in UK and USA compared to a quarter in all other countries. Around 30% claim to be “doing it themselves” whilst around 30% claim to be using a combination of service providers and in house disposal.
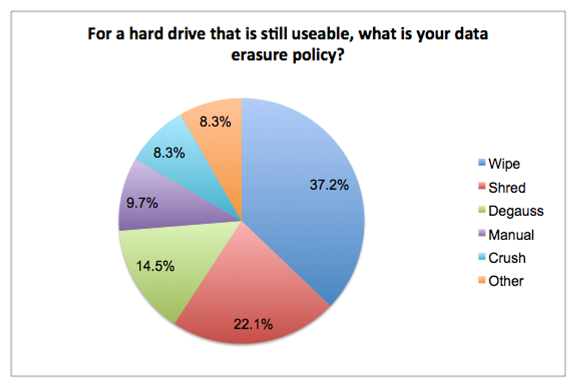
Hard drive disposal methods
Wiping was the most commonly cited method for hard drive data erasure. 64% of those who cited “wipe” as their data erasure policy were using this as a stand alone policy. i.e. 36% of those wiping devices were also going on to crush / shred devices. Industry standards generally recommend wiping, wiping is also the most environmentally friendly option as it allows potential reuse. See the “Further reading” section below for further information on wipe standards and best practices.
Measuring the quality of asset disposal service providers
ITAM Review readers had many and varied ways of gauging the quality of their asset disposal partners. The most common practices included auditing the quality of service, performing spot checks or visiting the providers premises unannounced. Certificates of destruction or disposal were also used, but not universally. Some readers cited the industry certifications of the provider and some simply stated they used general market information and customer references.

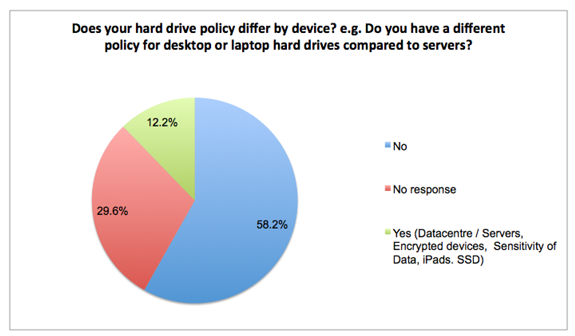
Industry Standards for Hard drive disposal
61% of respondents stated no specific industry standard they were following for hard drive disposal. 18.1% referred to DOD and 10.5% NIST. A collection of other ISO standards and industry references were also mentioned.
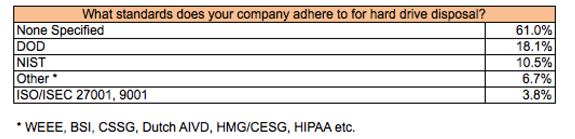
Proof of hard drive disposal
If an ITAM Review reader were asked to prove that a drive had been disposed, the most common response was to refer to the destruction or disposal certificate. Worryingly 29.5% had no way of proving disposal (or did not respond), 23.8% would refer to the disposal audit logs and a tiny minority (3.8%) took a photo or video of the destruction as proof.
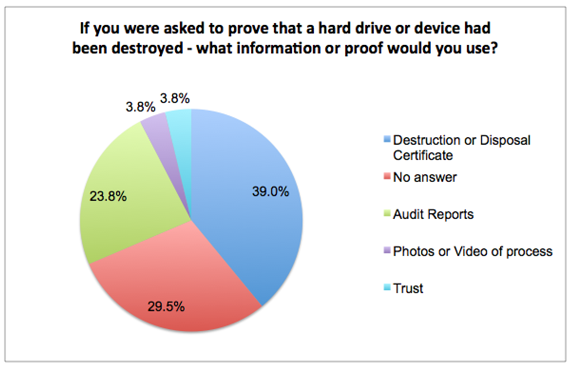
Disposal by type of device
Finally, we asked ITAM Review readers if their policy for hard drive disposal differed by device type. 58.2% cited the same policy regardless of device type, 12.2% said their policy differed – mainly because datacentre / servers were treated differently. But encryption, the sensitivity of data and device hurdles such as Ipad or SSD cards were cited as reasons for a change in policy.
Other advice share on hard drive disposal
Other anecdotal advice shared by ITAM Review readers:
- Be wary of companies that promise “shredding” but use a piston punch methodology. If a piston punch is not done properly the drives are still recoverable. Also, if the company is taking away the drive remains you should ensure that they are certified for environmentally friendly materials disposal.
- We caught our disposal vendor trying to outsource destruction to third party. Caught different vendor in the past selling off old devices (PCs, laptops, monitors ) even though contract said not to do so.
- Documenting data destruction is essential but not sufficient. What a company wipes is important. What has not been proven wiped is harder to determine, but far more important. ITAM is guilty of sharing vanity metrics with uneducated executives (e.g. we retired XXX computer or XXXX LBS). I wish ITAM would start sharing the bad news. I wish they would share information about what they cannot effectively track. Only then will we receive the resources and support necessary to protect the enterprise. Cybersecurity professionals proudly discuss how many attacks per minute they encounter. It is no wonder they receive 70% of security dollars. ITAM professionals needs to speak up.
- I have been managing the ITAD process for nearly 10 years and have done business with most of the major Global ITAD providers and I have found the biggest issue with disposal to be lack of education. Lack of education specifically by senior management/executive management at each company regarding the potential impact of the end of life process (being either from a data leak or improper downstream disposal). Lack of education by the individuals facilitating the ITAD program for corporation. Too often price is the leading factor in decision making putting a high degree of RISK on a corporation as vendors are selected based on pricing only rather than by the services they provide. Additionally as I have inspected vendor facilities in Asia Pacific region, Europe, South and Latin America and Domestic. What I have discovered through the audit process is that the vendors are very willing to improve and work with a client, but most clients are only on site to take the vendor guided tour of a facility. The clients do not educate themselves on what constitutes good processing practices, on proper physical security, environmental stewardship and most importantly data security. The vendors have some responsibility to educate their clients, but clients need to educate themselves or they will never be able to measure the quality of a service provider.
- Really sensitive drives are rare, and I take great pleasure in hammering them myself 🙂 Fewer than 1 per year, unfortunately. I could use the exercise.
- Solid state devices (SSD) introduce new challenges as well as cloud storage. HDDs cannot be the only focus as SSDs increase in capacity, shrink in size and take on new, unfamiliar shapes – including on board storage. Data is becoming increasingly mobile. Information security, protecting company/personal confidential data and intellectual property requires much broader thinking and keeping up with current technology.
- The one thing that I wish our company would do is wipe the hard drives before destruction while they are waiting to be destroyed. At times they are in transit to our location from another location and are not wiped before hand.
- This is something that we have struggled with for several years and the policies and procedures took approximately 2 years to get in place. The biggest issue we still have is with drives that must go back to a Vendor for Warranty.
- We also track printers that contain hard drives. We prefer to crush onsite and own a crusher; however, with the volume of systems, we often have to rely on 3rd party. We also require chain of custody documentation from our recycler.
- We emphasis to reduce E-Waste to minimal (Reduce, Reuse & Recycle) Something similar to EU-GDPR should be implemented across the globe.
- We have found our revenue share with our vendor is higher if the drives are erased instead of shredded and we are comfortable with erasure.
- What should probably be included in this type of program, is unscheduled visits to third party provider and observe the disk destruction process for you company’s systems and for other companies.
Further Reading
- USA Department of Defense (DoD) 5220.22 Wipe Standard
- USA National Security Agency (NSA) Media Destruction Guidance
- NIST 800-88 (Guidelines for Media Sanitization, 2006)
- NIST 800-88 (Guidelines for Media Sanitization, Revision 1, 2014)
- Best practices for media destruction, Cornell University
- UK National Health Service (NHS) – Destruction and disposal of sensitive data, good practice guidelines, 2017
- Quick guide to DoD 5220.22-M, US DoD 5220.22-M (ECE)
- UK Information Commissioners Office (ICO) “IT asset disposal for organisations” 2012
- Data Erasure on Wikipedia
- Quick Guide to Asset Tagging (ITAM Review)
- Asset Labeling Quick Guide (ITAM Review)
If you can recommend any further resources please contact me or leave a message in the comments below.
Utilities
- Sdelete (Microsoft)
- Dban (Free for personal use)
- Mac secure erase utility (Apple)
- AxCrypt (File Encryption)
- Eraser (Wipe)
- Gaijin (Wipe)
- Blancco (Enteprise Grade Erasure)
- Jetico (Encrypt and Wipe)
- 2BrightSparks (Encrypt and Wipe)
- Killdisk (Hard disk eraser)
- Bitraser (Data erasure)
- Certus Software
If you can recommend any further utilities or have feedback on the utilities above please contact me or leave a message in the comments below. Thanks again to everyone who took time to share their views.
Related articles:
About Martin Thompson
Martin is also the founder of ITAM Forum, a not-for-profit trade body for the ITAM industry created to raise the profile of the profession and bring an organisational certification to market. On a voluntary basis Martin is a contributor to ISO WG21 which develops the ITAM International Standard ISO/IEC 19770.
He is also the author of the book "Practical ITAM - The essential guide for IT Asset Managers", a book that describes how to get started and make a difference in the field of IT Asset Management. In addition, Martin developed the PITAM training course and certification.
Prior to founding the ITAM Review in 2008 Martin worked for Centennial Software (Ivanti), Silicon Graphics, CA Technologies and Computer 2000 (Tech Data).
When not working, Martin likes to Ski, Hike, Motorbike and spend time with his young family.
Connect with Martin on LinkedIn.

A common misconception is that a Certificate of Destruction transfers liability associated with data privacy laws to the data destruction vendor. A COD does NOT transfer liability – the original keeper of information is 100% responsible and liable. How do you efficiently destroy data to prevent a data breach after the drives are retired?
1) have hard drives shredded at your location where multiple employees can witness and verify – this step eliminates the need for “spot checks” or “surprise visits” that take time and coordination, 2) hire a third-party vendor that is certified by an internationally recognized organization – the certification is your due-diligence required by data privacy laws and 3) physically shred hard drives – the residual value is nothing compared to the cost of a data breach.
All data on Solid State Drives (SSD) should be encrypted for the whole life of the SSD if they are not going to be destroyed at the end of life – this is because SSDs have sophisticated management systems that maintain how many times a sector is written – this prevents full overwriting of the drive by utilities such as those listed above.